Infolinks In Text Ads
Tuesday, December 29, 2009
Twitter Decides to Take Password Security Seriously
"Twitter has hard-coded some 370 words in its sign-up page that are not allowed to be used as passwords for new accounts. The list is a good addition to the password strength algorithm already implemented, but it raises several questions about its source.
There is no secret that many Internet users still employ dictionary words and easy to guess names as passwords, even for their important accounts. Back in September, we reported that an analysis performed by a security enthusiast on a database of over 850,000 accounts revealed highly insecure passwords habits.
The aforementioned study showed that 3.5% percent of people used their first name as password, while 1.6% used their last one. The notorious '123456' string was chosen by 2% of users and 0.5% settled for 'password' as their access code. Fortunately, Twitter's list of banned passwords includes both of them.
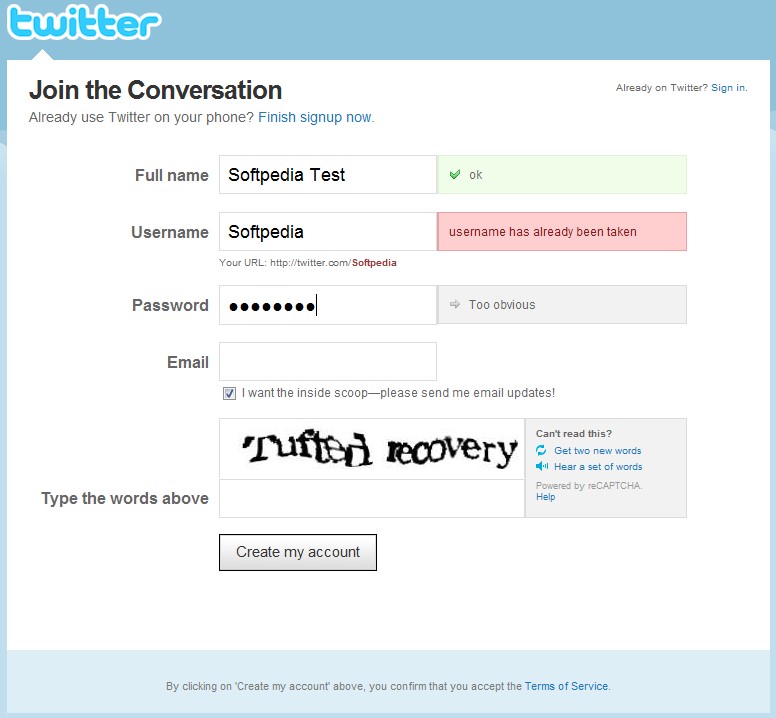
Rejected password on Twitter sign-up form
Enlarge picture
In addition to common dictionary words, the list also includes the names of popular TV shows, characters, sports teams, brands, places. However, security researchers note that it is quite different from other similar lists used for brute force attacks.
'It's not clear yet where the folks at Twitter got their list of banned passwords from but it occurred to me that it might be interesting to compare it to another list of common passwords, this time a list that the bad guys are using, the 246 passwords used by Conficker,' wrote Richard Wang of SophosLabs US. The result was that the two lists only have 29 passwords in common.
After removing the strings under six characters from the Conficker list, which wouldn't be accepted as passwords on Twitter by default, the researcher concludes that there are still '117 passwords that malware authors think are common but apparently Twitter does not.'
Others like TechCrunch, which reported about the list, wondered if the company compiled it by analyzing the history of password use on its own service. If that was the case, then they missed at least one, which they most certainly shouldn't have - 'happiness.'
This word was used for authentication by a Twitter support staffer named 'Crystal,' whose account was compromised through brute force by an 18-year-old hacker at the beginning of this year. This allowed the attacker to hijack 33 high profile Twitter accounts, including the ones of Britney Spears, Barack Obama, Rick Sanchez, or Fox News. Ironically though, the word 'crystal' made it to Twitter's list.
The complete list can be viewed by searching the source code of Twitter's sign-up page for 'twttr.BANNED_PASSWORDS.'"
Monday, December 28, 2009
Talented Programmer Gets Two-Year Prison Sentence in TJX Case
"Stephen Watt, a 25-year-old software developer, was sentenced to two years in a federal prison for the role he played in the TJX hit, one of the largest credit card thefts in history. The programmer was also ordered to pay the company $171.5 million in restitution for the harm caused.
The man befriended notorious hacker Albert Gonzales, the mastermind behind the TJX attack, while he was still in highschool. The two met online and were driven by their passion for computers. The programmer went on to work as software engineer for financial institutions dealing in the securities market, including Morgan Stanley.
Watt assisted Gonzales and his friends by creating a hacking program called 'blabla,' which was used to sniff out credit card information passing through the TJX computer network. This program was found by authorities on two separate servers in Latvia and Ukraine, along with the stolen details of millions of credit cards.
The programmer was indicted in November 2008, and the prosecutors said that 'On diverse dates, Watt modified for Albert Gonzales and provided him a sniffer program used by the conspirators to monitor and capture data traveling across corporate networks.' According to Wired, when authorities caught up with him, Watt worked at Imagine Software, a company developing real-time trading programs, where he earned around $130,000 per year.
The hit on TJX, or 'Operation Get Rich or Die Tryin' as Gonzales himself called it, involved stealing credit card information from the networks of major retail stores like T.J. Maxx, OfficeMax, Boston Market, Barnes & Noble, Sports Authority or Forever 21. The authorities called it 'the largest identity theft in our nation’s history' and TJX, the parent company of the retail chains, estimated its losses at $200 million.
Albert Gonzales, who at one time operated as an informant for the Secret Service, is also awaiting sentencing and could face as much as 17 years in prison for his role in the operation."
Wednesday, December 23, 2009
Unhide Friend in FaceBook
In FaceBook
Click on that and it should pop up any hidden friends, ask if you want to add them back to your news feed.
Just hit yes and you should be able to view the feeds from the friends too.
Monday, December 21, 2009
Heartland Settles with AMEX for $3.6 Million
"Heartland Payment Systems has reached a settlement with American Express, following the major security breach suffered by the company last year. According to the agreement, the payment processor will pay $3.6 million to the card brand.
Heartland Payment Systems is a Princeton-based provider of payment processing services for over 250,000 companies. In January 2009, it announced that its computer network had been breached and transaction data including credit card details had been stolen. The company found data sniffing applications installed on its computer systems during a 2008 audit.
In March, Visa removed Heartland from its list of providers compliant with the payment industry's security standards, PCI DSS. The firm has worked hard to get re-certified and has since been an active advocate for the use of end-to-end encryption across the payment industry.
Heartland's CEO, Robert Carr, previously announced that the company had set aside $12.6 million to be used to cover all costs related to the incident. This latest settlement with AMEX will be paid off from that reserve. Over half of the sum was claimed by Mastercard alone, but Carr noted at the time that it would challenge their fines in court. Meanwhile, Visa only fined the company for $1 million.
'We are pleased to have reached an equitable settlement with American Express,' commented Carr. 'This settlement marks the first agreement with a card brand related to the intrusion,' he added. The sum resolves all intrusion-related issues between the two parties, such as the costs incurred by AMEX to cancel and re-issue millions of credit cards.
It has also faced a class-action lawsuit filed by shareholders, who claimed that the management had lied about the state of security at the company in a conference call following the incident. The lawsuit was dismissed this month by Judge Anne Thompson of the New Jersey U.S. District Court."
German Government to Help Rid Computers of Malware
"The German government plans to launch a major botnet-cleaning operation in the country in 2010. ISPs will identify and contact the owners of infected computers and a specialized call center will be created to offer assistance with cleaning the malware.
The project is a joint initiative of the German Federal Office for Information Security (BSI) and eco, the Association of the German Internet Industry. The plan was announced on December 8, during the fourth national IT-Summit in Stuttgart and the advisory center is scheduled to go live in 2010.
The strategy is aimed at moving Germany out of the top 10 countries harboring malware. According to recent studies, the country currently occupies the third spot on a list that ranks countries by the number of infected hosts and the planners estimate that one in four German computers is currently infected.
If the project becomes a reality, the German ISPs will take it upon themselves to detect infected computers, most likely by watching connections to known botnet command and control servers. The owners of the compromised systems will first be notified via telephone or post and directed to a special website, which contains tools and advice for removing malware.
If the user fails to resolve the problem using the information on this website, they will receive a code to use when calling a specialized call center. This center will be funded by the government and will employ 40 IT specialists. No costs have been revealed so far.
The plan raises some concerns, as it is illegal in Germany to intercept Internet communications. However, the country's Telecommunications Act does allow ISPs to do it if the traffic represents a threat to their systems. Some bloggers go as far as calling it a subsidy for Microsoft, because it discourages users from looking into more secure operating systems such as Linux.
ISPs taking a pro-active role in the fight against malware is seen as something good by the infosec community, which has long criticized their passive approaches. Comcast, one of the largest Internet providers in the U.S. is testing an in-browser notification system, which automatically alerts infected customers and directs them to a website with malware-cleaning instructions and tools."
Thursday, December 17, 2009
Avatar Review
Avatar (2009)
Evil Tribal’s wants a valuable resource from another Tribal’s. So they send an infiltrator to another tribal, who make ups like the Tribal. He goes in and learns their way of living and find the valuable resources location.
Mean while he get attached to these people and the way of living. Then the Evil tribes attack the other and destroy their home. Then the tribe came to know about the infiltrator and they send him out. The infiltrator comes back and reunites the tribe and fights back to the evil tribes and send the evil tribe back to their home.
Evil Tribe is nothing but People from Earth and Another tribe is Navi's in Pandora.
This can be resembled in many Indian movies story, but the change is this has been taken with new technologies and planets. This is typically a commercial movie, with fantasy and animation alone.
When the movie started, I thought am going to enter into a new world and enjoy the movie. The first was very slow and made me sleep for a while in between the movie. Any way the second half went on fast and at the end, the movie was not up to the expectations.
Monday, November 23, 2009
Symantec Online Store Hacked
"A self-proclaimed grey-hat hacker has located a critical SQL injection vulnerability in a website belonging to security giant Symantec. The flaw can be leveraged to extract a wealth of information from the database including customer and admin login credentials, product serial numbers, and possibly credit card information.
The flaw was found by a Romanian hacker going by the online handle of Unu, according to whom an insecure parameter of a script from the pcd.symantec.com website, allows for a blind SQL injection (SQLi) attack to be performed. In such an attack, the hacker obtains read and/or write permission to the underlying database of the vulnerable website.
During a regular SQLi attack, the result of a rogue SQL query is displayed inside the browser instead of the normal web page output. Meanwhile, in a blind SQL injection, the query executes, but the website continues to display normally, making it much more difficult to extract information.
The content of the pcd.symantec.com website is written in Japanese, but from what we could determine, it serves a product called Norton PC Doctor. Accessing most of the website's sections requires authentication, and in order to exploit the blind SQLi vulnerability, the hacker had to use a few specialized tools. The Web server appears to be running Windows Server 2000 as operating system, Microsoft IIS 6.0 with ASP support and Microsoft SQL Server 2002 as database back-end.
From the screen shots released by Unu there are many potentially interesting databases, but the one he chose to look at is called 'symantecstore.' One of the tables in this database is named 'PaymentInformationInfo' and contains columns such as BillingAddress, CardExpirationMonth, CardExpirationYear, CardNumber, CardType, CcIssueCode, CustomerEmail, CustomerFirstName, CustomerLastName or SecurityIndicator.
Database listing on Symantec PC Doctor server
Enlarge picture
Unu claims that his interest is only to point out security issues and not misuse any data. Therefore, according to him, he did not attempt to extract any information from this table. Instead, he focused on another one called TB_MEMBER, which contains 70,356 records.
For demonstration purposes, he extracted 6 of these entries at random, revealing customer names and login credentials with the passwords stored in plain text; a major security oversight. The hacker also notes that passwords for the accounts in a different table called TB_EMPLOYEE are also stored in a similar insecure way.
A third table Unu chose to investigate is called TB_ORDER and contains columns such as ProductName, ProductNumber, SaleAmount and SerialNumber. There are 122,152 entries in the SerialNumber column.
This is not the first time when Unu scrutinizes the security of websites belonging to antivirus vendors. His previous targets includes Kaspersky and Bitdefender. Some months back, he even disclosed a vulnerability affecting a different Symantec website. The AV company eventually played down its impact.
At the end of his most recent disclosure, Unu mentions his previous attack against Kaspersky's US online store website. 'There was fair play, they quickly secured vulnerable parameter, and even if at first they were very angry at me, finally understood that I did not extract, I saved nothing, I did not abused in any way by those data found. My goal was, what is still, to warn. To call attention [sic.],' the hacker writes on his blog.
Note: We have alerted Symantec about the potential security breach. We will update this article when/if more information becomes available.
Update: In an e-mail to Softpedia, Symantec has confirmed the existence of a vulnerabiliy in the pcd.symantec.com. Here is the full statement we received:
'A SQL injection vulnerability has been identified at pcd.symantec.com. The Web site facilitates customer support for users of Symantec's Norton-branded products in Japan and South Korea only. This incident does not affect Symantec customers anywhere else in the world.
'This incident impacts customer support in Japan and South Korea but does not affect the safety and usage of Symantec's Norton-branded consumer products. Symantec is currently in the process of updating the Web site with appropriate security measures and will bring it back online as soon as possible. Symantec is still investigating the incident has no further details to share at this time.'"
Source Softpedia
Wednesday, November 18, 2009
10 Solid Tips to Safeguard Your Facebook Privacy
This guide will show what you can (and cannot) do to safeguard your Facebook privacy.
1. Organize Friends in Lists
What do you do when your boss, mother-in-law, or a casual web acquaintance sends you a friend request on Facebook? Use Friend Lists. Friend Lists are the foundation of your Facebook privacy settings. Select Friends from the top menu, and use the Create link to create friend lists like Co-workers, Family, College Friends, etc. Your friends can’t see your lists, so you can name them whatever you like.
Tip: On your left sidebar, all your friend lists may not show up by default. Click More to see all of them, and drag and drop those you want above the separator.
2. Customize Profile Privacy
Click Settings > Privacy Settings > Profile. Select which parts of your profile will be seen by whom.

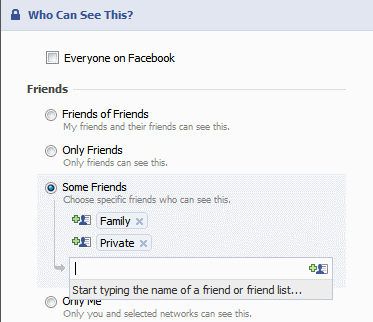
If you choose Customize in the drop down, you can be more specific. This is where the Friend Lists you created before become really useful.
Also go to the Contact Information tab and choose how you want your contact information to be shared on the Internet.
3. Set Facebook Privacy Level of Photo Albums
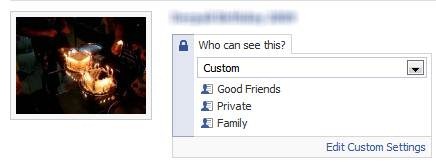
On the Photos tab of your profile page, click Album Privacy. Here again, you can use your Friend Lists to set the privacy for each photo album.
Note that your profile pictures go into a special album that is always visible to ALL your friends.
4. Restrict Search Visibility
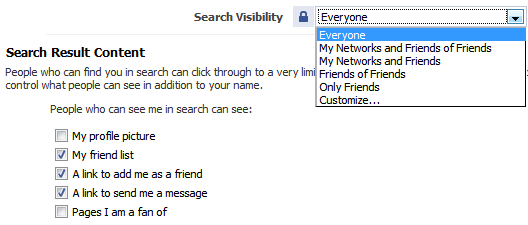
Click Privacy > Search to set your visibility when someone searches Facebook for people. This is an important way to safeguard your Facebook privacy. You can also select what will be visible in the search results.
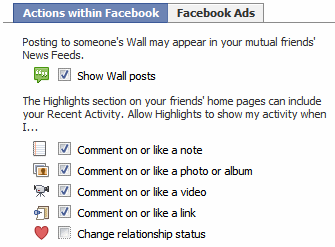
5. Control Automatic Wall Posts and News Feed Updates
Your actions in Facebook such as comments, likes, appear as highlights on ALL your friends’ home pages. You cannot use friend lists here, only turn them on or off.
Go to Privacy > News Feed and Wall and choose whether you want your boss or ex-girlfriend to know that you’re in a relationship.
6. Set Facebook Wall Privacy
Go to your profile page, click Options > Settings under the status box.
Here you can control whether your friends can post to your Wall, and who can see the posts made by your friends.
7. Avoid Appearing in Advertisements
Facebook has two types of advertisements: third-party and Facebook. Third-party advertisements are currently not allowed to use your pictures, but there is a setting to disallow it if it is allowed in the future. Go to Privacy > News Feed and Wall > Facebook Ads tab to turn this off.
The Facebook ads shown to your friends are about ‘social actions’ like becoming a fan of something. You can turn this off at the bottom of the page.
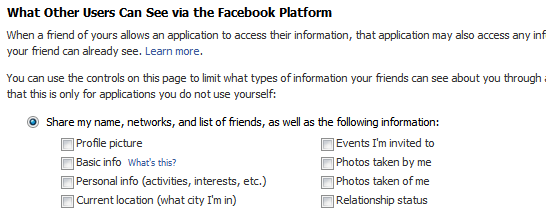
8. Protect Yourself from Friends’ Applications
Go to Privacy > Applications, and click the Settings tab and uncheck all the boxes. These settings control what information about you is visible to applications installed by your friends. By default, these are set to visible. This means that your religious, sexual, and political preferences, pictures, etc. are readily available to one of the million worldwide Facebook application developers, each time any of your friends takes a quiz, plays a game, or runs any other Facebook app. This is obviously a Facebook privacy issue.
This is the most commonly misunderstood aspect of Facebook privacy. These settings control what applications installed by your friends can see about you, even if you don’t install the application yourself.
Why is this important? Because these settings will not change anything about what you are sharing with the applications you install yourself. For that, go to the next step.
9. Privacy from Your Applications
There is no way to control what applications see about you; it is an all-or-nothing affair. Take this quiz developed by the American Civil Liberties Union to check what anonymous application developers can know about you and your friends each time you take a quiz.
The Burton Group’s Identity Blog features the Facebook Privacy Mirror, an application that you can use to find out what applications know about you and your friends. If you really want to see exactly what profile data of each of your friends is visible to application developers, Privacy Mirror shows it in detail.
The only thing you can do is to authorize only those applications you require and trust. Go to Settings > Application Settings from the top menu. Change the drop-down from Recently Used to Authorized. Here you can see all the applications you have authorized to get access to ALL your profile information. Remove the ones you no longer need.
Also check the list of applications Allowed to Post and Granted Additional Permissions to remove unwanted ones.
10. Quitting Facebook? Delete, Don’t Just De-Activate Your Account
You can easily deactivate your account in Facebook from the Settings page. But deactivation will retain all your profile information within Facebook, including pictures, friends, etc. If you want to permanently delete your Facebook account, click here to submit a deletion request. Note that:
- There is an unspecified delay between submitting your delete request and actual deletion.
- If you login to Facebook, your deletion request is automatically cancelled.
- There doesn’t seem to be any way to confirm that your request was completed.
- Even after permanent deletion, Facebook says that copies of your photos may remain on their servers for technical reasons.
Also, note that once in a while, there is news of a Facebook hack or leak that can expose your information on the Internet. It is better to be safe than sorry by avoiding using Facebook for anything that may embarrass you.
I hope this article gives you a better understanding and insight into Facebook’s privacy.
Wednesday, November 11, 2009
RBS WorldPay Hackers Indicted - After stealing over nine million dollars in a sophisticated attack - Softpedia
Back in December 2008, close to the winter holidays, a major US-based payment processor called RBS WorldPay announced that its network and computer systems were breached by unknown attackers. The company, which is operated by the Royal Bank of Scotland Group, said at the time that only around 100 re-loadable payroll cards had been misused and subsequently disabled.
However, what the company failed to note is that some of the compromised cards were actually used to steal a whooping nine million dollars. Not only that, but the impressive sum was withdrawn over a 24-hour period from over 2,100 ATMs located in at least 280 different cities worldwide, making this attack one of the most organized and sophisticated of its kind ever to be instrumented.
The indictment reveals that the hackers intercepted and cracked encrypted data passing through the network, after which they artificially inflated the limits of the accounts chosen as targets. The payroll card details including PIN numbers were then distributed to people across the world, known as cashers, who manufactured copies of the cards and used them on ATMs.
These co-conspirators allegedly kept between 30 and 50 percent of the money, while the rest was sent back to Sergei Tsurikov, 25, of Tallinn, Estonia, Viktor Pleshchuk, 28, of St. Petersburg, Russia, Oleg Covelin, 28, of Chisinau, Moldova, and a yet unidentified individual known only as 'Hacker 3,' who are named as the leaders of the gang and the hackers responsible for the breach.
Four other residents of Tallin, Estonia, in the persons of Igor Grudijev, 31, Ronald Tsoi, 31, Evelin Tsoi, 20, and Mihhail Jevgenov, 33, were indicted in connection with this scheme for withdrawing cash using cloned cards. Two unnamed individuals were also arrested for playing a similar role in Hong Kong. However, given the scope of this operation, this is only the beginning of a very long list of co-conspirators.
'The charges brought against this highly sophisticated international hacking ring were possible only because of unprecedented international cooperation with our law enforcement partners,' noted Assistant Attorney General of the Criminal Division Lanny A. Breuer. FBI Atlanta Field Office Special Agent-in-Charge Greg Jones added that this success sends 'a clear message to cyber-criminals across the globe. Justice will not stop at international borders, but continue with the on-going cooperation between the FBI and other agencies.'
Tsurikov, Pleshchuk, Covelin and 'Hacker 3' were charged with conspiracy to commit wire fraud, wire fraud, conspiracy to commit computer fraud, computer fraud, access device fraud and aggravated identity theft. Each of them face a sentence of over 35 years in prison and fines up to $3.5 million dollars. Meanwhile, Grudijev, Tsois and Jevgenov, who were indicted for access device fraud, risk maximum sentences of 15 years in prison and fines of up to $250,000."
NASA - 2012: Beginning of the End or Why the World Won't End?
Remember the Y2K scare? It came and went without much of a whimper because of adequate planning and analysis of the situation. Impressive movie special effects aside, Dec. 21, 2012, won't be the end of the world as we know. It will, however, be another winter solstice.
Much like Y2K, 2012 has been analyzed and the science of the end of the Earth thoroughly studied. Contrary to some of the common beliefs out there, the science behind the end of the world quickly unravels when pinned down to the 2012 timeline. Below, NASA Scientists answer several questions that we're frequently asked regarding 2012.
Question (Q): Are there any threats to the Earth in 2012? Many Internet websites say the world will end in December 2012.
Answer (A): Nothing bad will happen to the Earth in 2012. Our planet has been getting along just fine for more than 4 billion years, and credible scientists worldwide know of no threat associated with 2012.
Q: What is the origin of the prediction that the world will end in 2012?
A: The story started with claims that Nibiru, a supposed planet discovered by the Sumerians, is headed toward Earth. This catastrophe was initially predicted for May 2003, but when nothing happened the doomsday date was moved forward to December 2012. Then these two fables were linked to the end of one of the cycles in the ancient Mayan calendar at the winter solstice in 2012 -- hence the predicted doomsday date of December 21, 2012.
Q: Does the Mayan calendar end in December 2012?
A: Just as the calendar you have on your kitchen wall does not cease to exist after December 31, the Mayan calendar does not cease to exist on December 21, 2012. This date is the end of the Mayan long-count period but then -- just as your calendar begins again on January 1 -- another long-count period begins for the Mayan calendar.
Q: Could a phenomena occur where planets align in a way that impacts Earth?
A: There are no planetary alignments in the next few decades, Earth will not cross the galactic plane in 2012, and even if these alignments were to occur, their effects on the Earth would be negligible. Each December the Earth and sun align with the approximate center of the Milky Way Galaxy but that is an annual event of no consequence.
Q: Is there a planet or brown dwarf called Nibiru or Planet X or Eris that is approaching the Earth and threatening our planet with widespread destruction?
A: Nibiru and other stories about wayward planets are an Internet hoax. There is no factual basis for these claims. If Nibiru or Planet X were real and headed for an encounter with the Earth in 2012, astronomers would have been tracking it for at least the past decade, and it would be visible by now to the naked eye. Obviously, it does not exist. Eris is real, but it is a dwarf planet similar to Pluto that will remain in the outer solar system; the closest it can come to Earth is about 4 billion miles.
Q: What is the polar shift theory? Is it true that the earth’s crust does a 180-degree rotation around the core in a matter of days if not hours?
A: A reversal in the rotation of Earth is impossible. There are slow movements of the continents (for example Antarctica was near the equator hundreds of millions of years ago), but that is irrelevant to claims of reversal of the rotational poles. However, many of the disaster websites pull a bait-and-shift to fool people. They claim a relationship between the rotation and the magnetic polarity of Earth, which does change irregularly, with a magnetic reversal taking place every 400,000 years on average. As far as we know, such a magnetic reversal doesn’t cause any harm to life on Earth. A magnetic reversal is very unlikely to happen in the next few millennia, anyway.
Q: Is the Earth in danger of being hit by a meteor in 2012?
A: The Earth has always been subject to impacts by comets and asteroids, although big hits are very rare. The last big impact was 65 million years ago, and that led to the extinction of the dinosaurs. Today NASA astronomers are carrying out a survey called the Spaceguard Survey to find any large near-Earth asteroids long before they hit. We have already determined that there are no threatening asteroids as large as the one that killed the dinosaurs. All this work is done openly with the discoveries posted every day on the NASA NEO Program Office website, so you can see for yourself that nothing is predicted to hit in 2012.
Q: How do NASA scientists feel about claims of pending doomsday?
A: For any claims of disaster or dramatic changes in 2012, where is the science? Where is the evidence? There is none, and for all the fictional assertions, whether they are made in books, movies, documentaries or over the Internet, we cannot change that simple fact. There is no credible evidence for any of the assertions made in support of unusual events taking place in December 2012.
Q: Is there a danger from giant solar storms predicted for 2012?
A: Solar activity has a regular cycle, with peaks approximately every 11 years. Near these activity peaks, solar flares can cause some interruption of satellite communications, although engineers are learning how to build electronics that are protected against most solar storms. But there is no special risk associated with 2012. The next solar maximum will occur in the 2012-2014 time frame and is predicted to be an average solar cycle, no different than previous cycles throughout history."
Tuesday, November 10, 2009
Koobface Infiltrates Google Reader - Botnet hosted using Google Reader shared pages - Softpedia
Attackers employed Google Reader's possibility to share links and messages between users to host an image resembling a Flash video. Whenever the user tried to view the video, they were redirected to a cloned YouTube page containing a video. As in previous attacks, the user was soon prompted with an alert that invited them to upgrade their Flash player. Hidden was the fact that instead of the updated software, the user was downloading the doomed Koobface downloader component that would that take over the victim's computer.
Google was soon to react to these findings, taking all the necessary steps into blocking the infected URLs. Unlike previous attacks that used MySpace, Facebook and Twitter, this one seems not to have made the same type of impact, maybe thanks to Google's quick reaction and the fact that its users are a slight more Web-educated than all the social network users in the past.
The Mountain View-based company has recently found itself in the sights of many black hat attacks because of its bigger and bigger array of services that seems to provide more and more useful tools for hackers.
Previous incidents involved the Google App Engine and Google Groups service used as a botnet control and command center, the Google Apps service used as an illegal file sharing tracker, Picasa's email spam or attacks under the form of malware hosted inside video codec projects on Google Code.
The attacks come after Google introduced many services for safe Internet browsing, including the infamous blacklisting service Google Safe Browsing. This form of Koobface is still dangerous because its creators are now relying on Google's own reputation of a safe heaven for online users and attacking completely unsuspecting victims."
Monday, November 9, 2009
James Cameron’s ‘Avatar’ Cost $500M, May Flop - Analysts wonder whether one of the most expensive movies ever stands a chance at the box-office - Softpedia
According to the New York Times, if all this is handled well, then “Avatar” stands to make a profit and all the backers, sponsors and movie partners that invested heavily in it, as well as the cast and production crew actually get to make an extra buck aside from the fix salary they cashed in. However, in an industry that is seeing declining sales and shifting tendencies, it’s becoming harder and harder to predict whether a film has what it takes to sell at the box-office.
20th Century Fox, for one, as well as Cameron himself seem convinced that “Avatar” can turn a profit. What this means is that it has all the necessary ingredients to cover the $500-million budget it required to make – and then some. 3D theaters will hopefully cover some of that number of tickets the film needs to sell (with theaters being able to charge extra), DVD sales and merchandise will eventually work together to make a profit – and keep everybody involved happy, the NY Times piece says.
Cameron has already taken the extra steps to ensure things work out well. “In a further hedge, Mr. Cameron would give up part of his own participation in the film’s returns if production costs exceed a specified level, according to those who were briefed on the film. If final production costs exceeded $300 million, for instance, Mr. Cameron would effectively defer much of his payout until the studio and others were compensated, despite his years of labor on the movie.” the aforementioned publication informs.
However, it could very well be that it’s too soon to tell. There are also too many players involved, and too many unknowns in the equation for analysts to be able to make an accurate estimation. “At what point the various partners in ‘Avatar’ would see profit from the film depends on what share of revenue each receives as the movie reaches theaters, then home video and other media around the world. If domestic ticket sales reach $250 million – a level broken in the last year by five films, including ‘Star Trek’ and ‘The Hangover’ – Fox and its allies would appear to be headed into the black.” the NY Times further says."
Source: http://news.softpedia.com/news/James-Cameron-s-Avatar-Cost-500M-May-Flop-126503.shtml
Major Security Hole Discovered on Facebook and MySpace - The oversight allowed account hijacking and theft of user data - Softpedia
The discovery was made while 24-years-old Dutch Web developer Yvo Schaap tried to find a workaround to a problem he was having with one of his Facebook applications. “I found a solution to one of my function limitations. Surprisingly, when looked into more carefully my solution allowed full access and control to the Facebook user account that accessed my application,” he notes on his blog.
As the programmer goes on to explain, this is not actually a bug, but an insecure configuration issue in crossdomain.xml. This file can be used to tell a Flash application, loaded from a URL and executed locally on the client, if it is able to access a file served from its domain. For example, if the owner of domain A wants to let an application from domain B access its files, it can specify domain B in the crossdomain.xml on its server.
While the crossdomain.xml on facebook.com whitelisted only other domains and sub-domains associated with Facebooks, the similar file on connect.facebook.com contained an <allow-access-from domain=”*” /> directive. This meant that any Flash application, hosted on any domain, was allowed to access data on the connect.facebook.com sub-domain.
“This wouldn't be a big deal if the subdomain only hosts images, but unfortunately this domain hosts the whole Facebook property, including a facebook user session,” Mr. Schaap notes. The web developer goes on to point out that if a user has auto-login enabled and is served with the URL to a specially-crafted flash file, an attacker could obtain full control of their account.
MySpace also suffered from a similar crossdomain.xml misconfiguration, though not as obvious as in Facebook's case. In particular, the crossdomain.xml on myspace.com granted access to a farm.sproutbuilder.com sub-domain. Sprout Builder is a web application building platform, which amongst other types of media, allows its clients to upload and incorporate .swf (Flash) files into their projects. As it turns out, these files are hosted on farm.sproutbuilder.com, thus opening the opportunity to create MySpace self-propagating social networking worm.
Yvo Schaap contacted both companies in advance of making this public and they moved swiftly to address the security problems. However, if two of the biggest social networking platforms left such gaping security holes opened, it is reasonable to assume that many smaller websites also have them."
Source: http://news.softpedia.com/news/Major-Security-Hole-Discovered-on-Facebook-and-MySpace-126327.shtml
Computer Trojan Helped Expose Secret Syrian Nuclear Reactor - Which was subsequently bombed by Israel in September 2007 - Softpedia
Journalists from the German publication Der Spiegel have recently published an article describing the events that led and followed Israel's bombing of the Syrian nuclear reactor at Al Kibar. According to them, Israel had reason to believe that Syria might be planning to launch a secret nuclear program even since 2002, but information was scarce at the time.
Their suspicions intensified in 2004 after United States' National Security Agency (NSA) informed them of an unusually high number of calls between Pyongyang, the capital of North Korea, and a region in the Syrian desert situated close to the Euphrates river. This place was called Al Kibar.
Then, in late 2006, Mossad operatives succeeded in obtaining more concrete evidence. Apparently, this was achieved by installing a professional trojan on the computer of a senior Syrian government official. The clandestine program was planted on his laptop left in a Kensington hotel room during a trip to London.
The trojan stole secret documents and images depicting the Al Kibar reactor in various stages of construction. It also captured photos of Chon Chibu, a leading North Korean nuclear scientist, together with Ibrahim Othman, the director of the Syrian Atomic Energy Commission. This intelligence gathering effort eventually led to 'Operation Orchard,' the bombing by Israeli fighter jets of the Al Kibar complex in September 2007.
There is no mention as to whether the information on this laptop was encrypted or not, but generally with such sensitive information, it is. However, it doesn't matter as this is a perfect example of a so-called 'Evil Made' attack, a situation where the attacker can install a boot-level malware on an unattended device, which is then returned to the owner for use.
'People who encrypt their hard drives, or partitions on their hard drives, have to realize that the encryption gives them less protection than they probably believe,' warns cryptography guru Bruce Schneier. 'It protects against someone confiscating or stealing their computer and then trying to get at the data. It does not protect against an attacker who has access to your computer over a period of time during which you use it, too,' he explains."
Source: http://news.softpedia.com/news/Computer-Trojan-Helped-Expose-Secret-Syrian-Nuclear-Reactor-126423.shtml
Two Men Accused of Hacking Their Former Employer's Computers - Failure to suspend credentials at fault again - Softpedia
Scott R. Burgess, 45 of Jasper, Indiana, and Walter D. Puckett, 39 of Williamstown, Kentucky, were indicted on November 4 for computer intrusion, the United States Attorney's Office for the Southern District of Indiana announces. The pair used to work for Jasper-based Stens Corporation, a distributor of replacement parts for small engine outdoor power equipment.
After quitting their jobs at Stens in late 2004 and early 2005, respectively, Burgess and Puckett went on to work for a rival company. The authorities claim that until September 2006, the two illegally accessed private information stored on computers belonging to Stens Corporation on twelve separate occasions.
The intrusions allegedly had personal and commercial gain motivation and were instrumented through the use of old login credentials. It is also mentioned that Stens' IT staff noticed unusual behavior and disabled several passwords, however the perpetrators switched to using others.
According to Assistant U.S. Attorney Todd S. Shellenbarger, Burgess and Puckett face a maximum sentence of five years in prison and a fine of $250,000 each. The Federal Bureau of Investigation and the Indiana State Police have collaborated in the investigation.
Failure to disable the login credentials of dismissed individuals is a popular attack vector for data breach incidents. Security experts have warned that the risk of disgruntled employees hacking their way back in is even greater now due to the harsh economic environment.
Back in September, we reported that a former IT consultant pleaded guilty to accusations of damaging a critical system used to monitor underwater oil pipelines for leaks, because an oil-extraction company refused to offer him permanent employment. In August, a computer specialist was arrested and indicted for hacking into the network of a charity he used to work for and deleting donor records."
Source: http://news.softpedia.com/news/Two-Men-Accused-of-Hacking-Their-Former-Employer-s-Computers-126361.shtml
Sunday, October 25, 2009
Deal-breakers of our marriages
‘A fine marriage is like a fine wine. It improves with age.’ Of course yes…but after a wedding who cares to make it fine or how many are even ready to think about it?
In our system, normally all parents are worried more about the boy’s/girl’s family background in terms of caste, education, wealth and whether the family is labeled ‘good’. I wonder how they conclude that the family is ‘good’ or ‘bad’. Any ways, a wedding happens after scrutinizing most aspects and satisfying the majority of terms and conditions, if not all. Then, why do marriages fail several times…even the properly done arranged marriages? Many relationships end bitterly in a very shot time…why?
Even though the changing lifestyle is cited as one of major reasons, in my experience is not the real destroyer. Many elderly people are escaping from the real facts. If one observes the post-marital scenario closely, regular causes behind broken/sour marriages are mainly dowry issues, conflicts between the elders of both families or the girl and in-laws (interestingly not between the couple), sufferings in the hands of in-laws, labeled short-comings in the customs supposed to be followed by the girl’s side (in most situations the boy’s side can behave in the way they want or think is right). In the present society, where the girls and boys are treated equal in most aspects, why we are still sticking to many hopeless customs when it comes to marriage. Many times instead of bringing prosperity, these hopeless things are the deal breakers.
Have anybody ever bothered about speaking to the couple whether they feel fine after marriage, find out the problems they are facing may be in understanding each other and helping them in sorting the differences out? Huh, most elders don’t have enough time to watch the girl’s behavior, her family and criticize whenever possible. They are more bothered about whether her family respects (!) their son in the way they want and what has been done from her side for Aadi, Diwali and Pongal. Do they feel these are the aspects which can make a marriage fine?
They want the girl to follow their practices on her own. How will it happen from the next day of marriage…she should at least be made aware of what is expected from her isn’t? Does anybody bother to make her comfortable in the new environment, speak to her about her brought up/regular schedule, daily activities and tell her the need/importance of following the customs and practices in the new environment? Most in-laws however are more concerned about stabilizing their position in their son’s mind.
In our system, most of the times, two entirely unfamiliar people come together…sometimes the differences are huge. They need time first to understand each other better…am not saying that people should change their personalities…it’s about understanding first so that they can better adjust. But, before this happens, other aspects/issues peep in, which many times instead of strengthening a marriage, does the job of a destructor. The couple instead of strengthening their relationships starts quarrelling backing their family/parent’s stands. Customs are made for people but these days the reverse is happening.
And everybody involved, don’t be authoritative and don’t think you are superior. Please understand that everybody have the right to express and enjoy at least minimum freedom. Support us to live our lives
Wednesday, September 30, 2009
Increase ur followers in Twitter

You can increase your followers in Twitter using FastFollowers.
This site got 10 followers within an hour of time for me...
You can visit this site @ http://fastfollowers.com?ref=harikumaran
You can follow me on http://twitter.com/harikumaran
Thursday, August 27, 2009
Extensive Cellphone Use Leads to Brain Tumors
Check out more details on this Link
Tuesday, August 25, 2009
Life is little bit of Fun & lots of Tragedy
Some say when you are satisfied with what you have then you will not have worries.
One day you might have felt that you are the most happiest person in the whole world... But soon you would felt that your are very unluckiest person in the world...
This is how life goes on, when you expect something, you will never get it... but when you decide to leave it away... after few days or months... which ever you expected earlier will come to you automatically...
Life is always puzzle, no one know what will happen next. Except GOD... source of everything in the world.. Hope GOD give me a change soon...
Friday, August 21, 2009
Tata Tion

Tion comes in a 400 ml pet bottle with the Apple Buzz, Mango Rush and Peach Punch Flavor. The pet bottle is stylish and unique from other Juice pet bottles.
More than other drinks I prefer Tion now a days... Especially the Peach flavor is fantastic...
I became a Tion Fan :)
Wednesday, August 19, 2009
Opera Mini - Mobile Browser

Opera Mini Browser is specially made for Mobile users. This browser is very fast and effective in mobile browsing. I use this application in my Samsung E1410, which is a normal model without many features. But still the Opera Mini browser helps me in accessing my Gmail, Blogger, Orkut, Facebook and Twitter site easily...
The features are awesome in the mobile browser. More than anything its a open source application and its free to download. I love using this browser...
Even if I advanced featured mobile, I will try Opera Mini on the same...
You can download Opera Mini in the link Opera Mini
Symptoms of Swine Flu

Symptoms of swine flu are like regular flu symptoms and include fever, cough, sore throat, runny nose, body aches, headache, chills, and fatigue. Many people with swine flu have had diarrhea and vomiting. Nearly everyone with flu has at least two of these symptoms. But these symptoms can also be caused by many other conditions. That means that you and your doctor can't know, just based on your symptoms, if you've got swine flu. Health care professionals may offer a rapid flu test, although a negative result doesn't necessarily mean you don't have the flu.
You can watch the video related to the symptoms of Swine Flu in this link Swine Flu Symptoms
You can watch the precaution video in the link Safety Precaution for Swine Flu