Infolinks In Text Ads
Tuesday, December 29, 2009
Twitter Decides to Take Password Security Seriously
"Twitter has hard-coded some 370 words in its sign-up page that are not allowed to be used as passwords for new accounts. The list is a good addition to the password strength algorithm already implemented, but it raises several questions about its source.
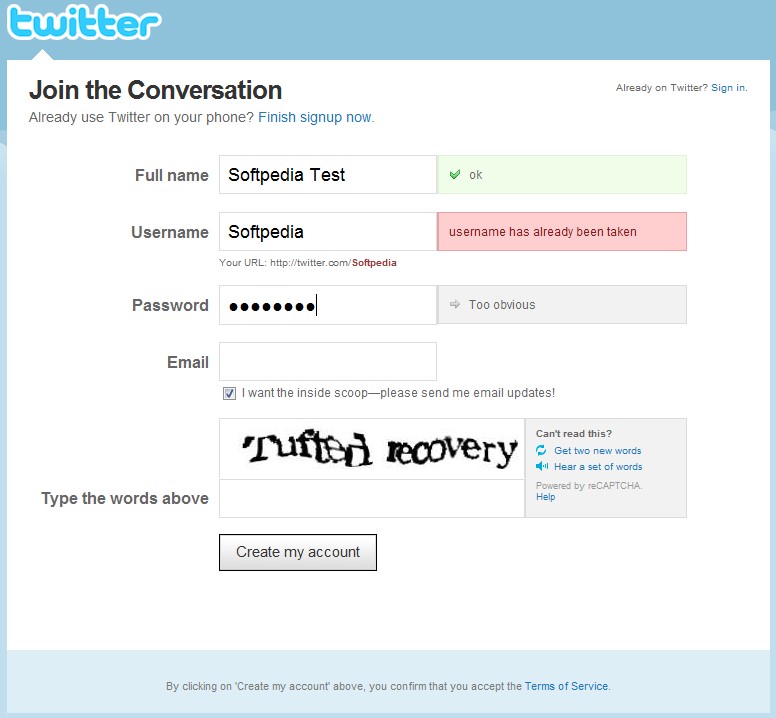
There is no secret that many Internet users still employ dictionary words and easy to guess names as passwords, even for their important accounts. Back in September, we reported that an analysis performed by a security enthusiast on a database of over 850,000 accounts revealed highly insecure passwords habits.
The aforementioned study showed that 3.5% percent of people used their first name as password, while 1.6% used their last one. The notorious '123456' string was chosen by 2% of users and 0.5% settled for 'password' as their access code. Fortunately, Twitter's list of banned passwords includes both of them.
Rejected password on Twitter sign-up form
Enlarge picture
In addition to common dictionary words, the list also includes the names of popular TV shows, characters, sports teams, brands, places. However, security researchers note that it is quite different from other similar lists used for brute force attacks.
'It's not clear yet where the folks at Twitter got their list of banned passwords from but it occurred to me that it might be interesting to compare it to another list of common passwords, this time a list that the bad guys are using, the 246 passwords used by Conficker,' wrote Richard Wang of SophosLabs US. The result was that the two lists only have 29 passwords in common.
After removing the strings under six characters from the Conficker list, which wouldn't be accepted as passwords on Twitter by default, the researcher concludes that there are still '117 passwords that malware authors think are common but apparently Twitter does not.'
Others like TechCrunch, which reported about the list, wondered if the company compiled it by analyzing the history of password use on its own service. If that was the case, then they missed at least one, which they most certainly shouldn't have - 'happiness.'
This word was used for authentication by a Twitter support staffer named 'Crystal,' whose account was compromised through brute force by an 18-year-old hacker at the beginning of this year. This allowed the attacker to hijack 33 high profile Twitter accounts, including the ones of Britney Spears, Barack Obama, Rick Sanchez, or Fox News. Ironically though, the word 'crystal' made it to Twitter's list.
The complete list can be viewed by searching the source code of Twitter's sign-up page for 'twttr.BANNED_PASSWORDS.'"
Monday, December 28, 2009
Talented Programmer Gets Two-Year Prison Sentence in TJX Case
"Stephen Watt, a 25-year-old software developer, was sentenced to two years in a federal prison for the role he played in the TJX hit, one of the largest credit card thefts in history. The programmer was also ordered to pay the company $171.5 million in restitution for the harm caused.
The man befriended notorious hacker Albert Gonzales, the mastermind behind the TJX attack, while he was still in highschool. The two met online and were driven by their passion for computers. The programmer went on to work as software engineer for financial institutions dealing in the securities market, including Morgan Stanley.
Watt assisted Gonzales and his friends by creating a hacking program called 'blabla,' which was used to sniff out credit card information passing through the TJX computer network. This program was found by authorities on two separate servers in Latvia and Ukraine, along with the stolen details of millions of credit cards.
The programmer was indicted in November 2008, and the prosecutors said that 'On diverse dates, Watt modified for Albert Gonzales and provided him a sniffer program used by the conspirators to monitor and capture data traveling across corporate networks.' According to Wired, when authorities caught up with him, Watt worked at Imagine Software, a company developing real-time trading programs, where he earned around $130,000 per year.
The hit on TJX, or 'Operation Get Rich or Die Tryin' as Gonzales himself called it, involved stealing credit card information from the networks of major retail stores like T.J. Maxx, OfficeMax, Boston Market, Barnes & Noble, Sports Authority or Forever 21. The authorities called it 'the largest identity theft in our nation’s history' and TJX, the parent company of the retail chains, estimated its losses at $200 million.
Albert Gonzales, who at one time operated as an informant for the Secret Service, is also awaiting sentencing and could face as much as 17 years in prison for his role in the operation."
Wednesday, December 23, 2009
Unhide Friend in FaceBook
In FaceBook
Click on that and it should pop up any hidden friends, ask if you want to add them back to your news feed.
Just hit yes and you should be able to view the feeds from the friends too.
Monday, December 21, 2009
Heartland Settles with AMEX for $3.6 Million
"Heartland Payment Systems has reached a settlement with American Express, following the major security breach suffered by the company last year. According to the agreement, the payment processor will pay $3.6 million to the card brand.
Heartland Payment Systems is a Princeton-based provider of payment processing services for over 250,000 companies. In January 2009, it announced that its computer network had been breached and transaction data including credit card details had been stolen. The company found data sniffing applications installed on its computer systems during a 2008 audit.
In March, Visa removed Heartland from its list of providers compliant with the payment industry's security standards, PCI DSS. The firm has worked hard to get re-certified and has since been an active advocate for the use of end-to-end encryption across the payment industry.
Heartland's CEO, Robert Carr, previously announced that the company had set aside $12.6 million to be used to cover all costs related to the incident. This latest settlement with AMEX will be paid off from that reserve. Over half of the sum was claimed by Mastercard alone, but Carr noted at the time that it would challenge their fines in court. Meanwhile, Visa only fined the company for $1 million.
'We are pleased to have reached an equitable settlement with American Express,' commented Carr. 'This settlement marks the first agreement with a card brand related to the intrusion,' he added. The sum resolves all intrusion-related issues between the two parties, such as the costs incurred by AMEX to cancel and re-issue millions of credit cards.
It has also faced a class-action lawsuit filed by shareholders, who claimed that the management had lied about the state of security at the company in a conference call following the incident. The lawsuit was dismissed this month by Judge Anne Thompson of the New Jersey U.S. District Court."
German Government to Help Rid Computers of Malware
"The German government plans to launch a major botnet-cleaning operation in the country in 2010. ISPs will identify and contact the owners of infected computers and a specialized call center will be created to offer assistance with cleaning the malware.
The project is a joint initiative of the German Federal Office for Information Security (BSI) and eco, the Association of the German Internet Industry. The plan was announced on December 8, during the fourth national IT-Summit in Stuttgart and the advisory center is scheduled to go live in 2010.
The strategy is aimed at moving Germany out of the top 10 countries harboring malware. According to recent studies, the country currently occupies the third spot on a list that ranks countries by the number of infected hosts and the planners estimate that one in four German computers is currently infected.
If the project becomes a reality, the German ISPs will take it upon themselves to detect infected computers, most likely by watching connections to known botnet command and control servers. The owners of the compromised systems will first be notified via telephone or post and directed to a special website, which contains tools and advice for removing malware.
If the user fails to resolve the problem using the information on this website, they will receive a code to use when calling a specialized call center. This center will be funded by the government and will employ 40 IT specialists. No costs have been revealed so far.
The plan raises some concerns, as it is illegal in Germany to intercept Internet communications. However, the country's Telecommunications Act does allow ISPs to do it if the traffic represents a threat to their systems. Some bloggers go as far as calling it a subsidy for Microsoft, because it discourages users from looking into more secure operating systems such as Linux.
ISPs taking a pro-active role in the fight against malware is seen as something good by the infosec community, which has long criticized their passive approaches. Comcast, one of the largest Internet providers in the U.S. is testing an in-browser notification system, which automatically alerts infected customers and directs them to a website with malware-cleaning instructions and tools."
Thursday, December 17, 2009
Avatar Review
Avatar (2009)
Evil Tribal’s wants a valuable resource from another Tribal’s. So they send an infiltrator to another tribal, who make ups like the Tribal. He goes in and learns their way of living and find the valuable resources location.
Mean while he get attached to these people and the way of living. Then the Evil tribes attack the other and destroy their home. Then the tribe came to know about the infiltrator and they send him out. The infiltrator comes back and reunites the tribe and fights back to the evil tribes and send the evil tribe back to their home.
Evil Tribe is nothing but People from Earth and Another tribe is Navi's in Pandora.
This can be resembled in many Indian movies story, but the change is this has been taken with new technologies and planets. This is typically a commercial movie, with fantasy and animation alone.
When the movie started, I thought am going to enter into a new world and enjoy the movie. The first was very slow and made me sleep for a while in between the movie. Any way the second half went on fast and at the end, the movie was not up to the expectations.